Imagine getting up one morning to find out that your contenders have got their hands on your business secrets! You would go into a cardiac arrest, won’t you? Losing the USP and business secrets is the last thing any business owner would want.
The cloud revolution is upon us, and it is here to stay. If the recent survey is right, then we can expect 83% of enterprises to go the cloud way by 2022. Can you imagine the vast amount of sensitive business data that would be sitting in the cloud network?
This creates the need to keep the cloud network secured from your end. Although the cloud network comes with unprecedented benefits like efficiency, productivity, and flexibility, it also comes with a flip side.
Since cloud networks are susceptible to data hacks, it becomes quite an assignment to keep the data protected. So how do you keep your business safe?
If you do not want your business data to be compromised, then I have some great tips for you. Use the same to thwart every attempt made by a cybercriminal.
10+ Safety Hacks for the Security of your Cloud Network
Here are the steps that you need to take to keep your business data vaulted safely.
Step 1: Practice Due Diligence
Understand the network you use. This is imperative so that you know how to provide functionality and security for the cloud-deployed applications that you use for your business. Here is what you can do.
1. Plan the Process-
The first step in building a successful cloud deployment is to select an appropriate application from a CSP. Start by developing a multiple-CSP strategy. Consider how the app that you use could be deployed to several CSPs. Also, read benefits of cloud computing for businesses.
2. Develop and then deploy
Application development and deployment involve the correct usage of CSP services in cloud applications. In case you are getting a new application developed for the cloud, make sure that you develop the app using the CSP guidance.
In the case of migration of an existing application, you must review its implementation from the CSP’s guidance and implement the changes to deploy the application properly.
3. Secure the operation
Once you have developed and deployed the application or the system, it is essential that you ensure that they are being operated securely. Since the software supports the virtual infrastructure of a cloud network, it can be managed in a source code control system.
4. Decommission
For cases like the discontinuation of the key services of the CSP, you must plan for decommissioning even before you deploy the applications.
Every cloud service is unique to each CSP which would make moving an application from one CSP to another a significant effort. It is therefore vital that your team knows how to extract data and migrate it from one CSP to another (if the need arises).
Step 2: Manage Access to Cloud
Access management consists of three phases. They are (a) the identification and authentication of users accessing the applications or the system, (b) the ability to assign access rights to users, and (c) the ability to enforce access control policies for resources.
1. Identify and Authenticate Users
I suggest that you use multifactor authentication to reduce the risk of data compromise. This way, an attacker has to acquire multiple authentication elements, thus buying you time and reducing the chances of cyber-theft.
2. Assign Access Rights to Users
Make a list of all the employees who need access to the cloud applications and system. Chalk out a plan to make sure that only the ones who have permission can access your data. Think biometric regulations for the purpose. Also, make sure that no person can harm your business by using your virtual data centre.
3. Enforce Resource Access Policies –
CSPs offer different types of storage services. Get access policies created for each of them. The policy for a virtual disk should differ from that of blob storage. Ask your team of software engineers to configure these service-specific access policies to protect the data you store on a cloud network.
Step 3: Data Protection
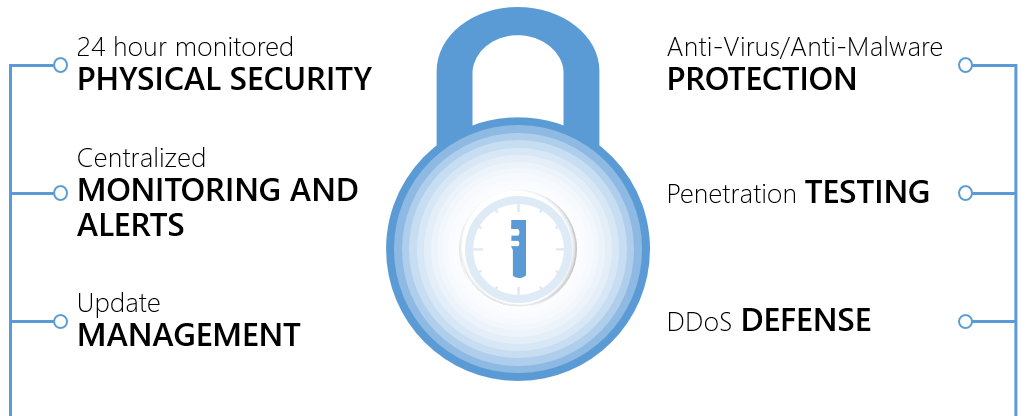
Image Source: https://docs.microsoft.com/en-us/azure/best-practices-network-security
The final step is that of data protection. It involves four separate challenges. They are (a) protecting the data from unauthorized access, (b) ensuring continued access to data in case of failures, and (c) Managing accidentally Deleted Data and (d) Monitoring Cloud-Deployed Resources.
1. Protection of Data against Unauthorized Access
Make sure that you encrypt data to protect it from disclosure by unauthorized access. CSPs offer a choice of CSP-managed keys for consumers. Apply these associated encryption keys to ensure effective encryption. Learn to manage and leverage API keys from the best in the business – Google Cloud.
2. Ensure Availability of Data
Cloud systems are not perfect and could result in accidental loss of customer data. You must ensure that you back up the data on your CSP so that you can recover processes as per the needs of your organization.
3. Manage Deleted Data
Quite often, CSPs tend to replicate data and hide them in deploy files. Ask your team to analyze the cloud files thoroughly to trace if sensitive data can be copied or cached.
Every time you delete sensitive data, follow the process of finding out the files where it may have been backed up and ensure that those copies are removed.
4. Monitor Cloud-Deployed Resources
The CSP generally monitors the services provided to the consumers. However, it may not be responsible for monitoring the systems you create using the services provided to you.
Therefore, you must rely on CSP-provided information to detect unauthorized access to the systems and applications you use in your business. You can also use it to trace unethical usage of your applications.
Conclusion
The cloud is always a hot target because of the intellectual property that it holds within itself. So, make sure that you develop a thorough understanding of the services before you invest in them.
For every two applications that you invest in, you must also spend your resources in buying effective cloud security management tools under CSP.
If your company falls under small or mid-sized organizations, then make sure that you use a mature CSP to reduce the risk of data theft on the cloud. What else do you think can work to keep a cloud network secured? You can share your ideas in the comments section below. We would be happy to get some extra tips.
