Serverless computing is increasingly changing the way applications are being developed, distributed, and run. For a lot of businesses, it can be a gamechanger.
But to be clear, while it may be called such, this execution model doesn’t exactly operate without a server. In serverless computing, the software code is outsourced to the cloud provider’s infrastructure, instead of on tower servers where the application is executed at scale, based on immediate and individual requests.
In this model, cloud providers like Amazon Web Services (AWS) and Google Cloud Platform manage resource allocation elastically as required.
This allows for flexibility in pricing where you only pay for the number of resources consumed as opposed to pre-purchasing units of capacity.
As such, they need to ensure that the infrastructure remains secure. This article is on the security challenges serverless architectures face, and what you can do to mitigate its effects.
The Rise of Serverless Architecture
If you’re just learning about the concept of serverless computing, let’s start with what it can do for your business. Migrating your IT environment to the cloud affords you diverse resources that are available at scale. This means that your enterprise can expand into the cloud using serverless architecture across public and private cloud environments.
This type of architecture has allowed enterprises to fully embrace digital transformations while benefiting from the opportunities brought about by the modernization of the application and infrastructure stack. This includes things like new modes of automation, management, DevOps, and security (more on this later).
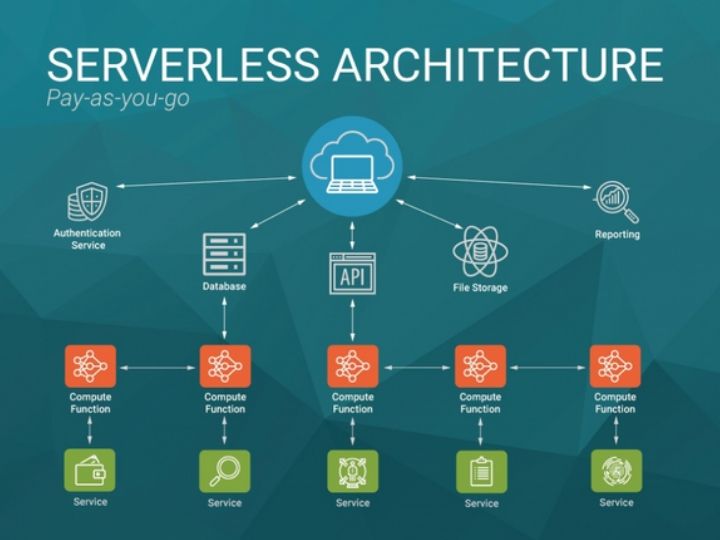
But to be clear, while it may be called such, this execution model doesn’t exactly operate without a server. In serverless computing, the software code is outsourced to the cloud provider’s infrastructure where the application is executed at scale, based on immediate and individual requests.
In this model, cloud providers like Amazon Web Services (AWS) and Google Cloud Platform manage resource allocation elastically as required. This allows for flexibility in pricing where you only pay for the number of resources consumed as opposed to pre-purchasing units of capacity.
Also Read: Simple Steps Towards Better Internet Security
Cybersecurity Stats You Need to Know
As it’s such a dynamic digital trend, serverless environments will inevitably be targeted with malicious intent. Here are some of the more notable numbers you should know.

- The FBI Internet Crime Complaint Centre reported receiving 23,775 complaints in 2019 from compromised emails alone, with calculated losses amounting to $1.7 billion. Overall, some $3.5 billion were lost globally from cybercrime.
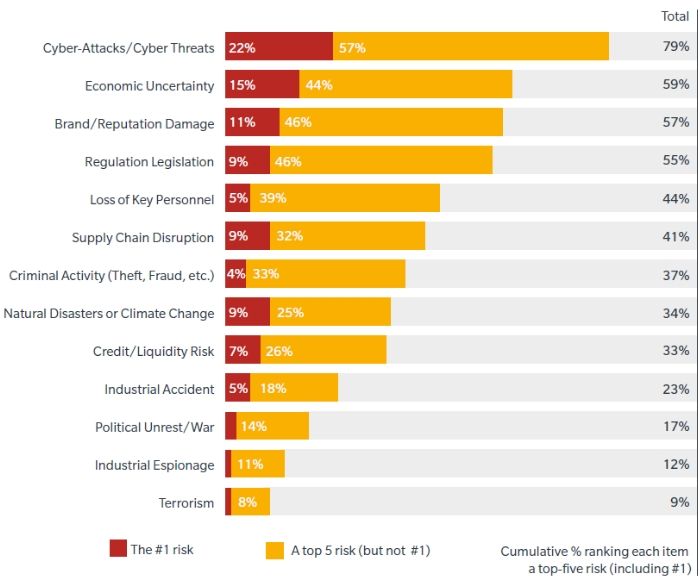
- In a global cyber risk perception survey conducted by Microsoft, 79% of the respondents said that cyber threats/attack is the biggest concern in their organization.
- Speaking of digital environments, a Juniper Research report forecasts online payment fraud to cost eCommerce at least $25 billion annually by 2024, a terrifying prospect for virtually all businesses. It’s no surprise then that 73% of leading organizations consider strong cybersecurity as a key contributor to business success.
- According to a study by the Ponemon Institute, cyberattack prevention initiatives could save businesses up to 82% of the costs associated with the cybersecurity lifecycle (prevention, detection, containment, recovery, and remediation).
- Interestingly enough though, the same study found that 76% of security professionals focus on detection and containment instead of prevention. They point to containment being more accountable than prevention.
5 Ways to Mitigate Serverless Security Threats
So now that you have an idea of how much of a financial hit organization can suffer from cyberattacks, here are a few tips on how you can minimize risks.
1) Maintain a good monitoring and logging system

When you don’t have a good monitoring system and a contextual logging mechanism (where, what, how), you run the risk of decreasing awareness and in-time monitoring and response to threats. Additionally, you can end up with a broken application without a clue of what went wrong.
What you can do:
While this is, admittedly, still a challenge for serverless apps, you can put all support services providers like AWS have to offer like.
This includes features like AWS X-Ray, which increases transparency into serverless execution by visualizing the execution path and making logs more easily accessible.
CloudWatch, meanwhile, can provide both logging and monitoring alerts that can increase visibility, and make both debugging errors and threat detection easier.
2) Limit/Avoid third-party dependencies
It’s hard to monitor dependencies of functions that rely on third-party software like open-source libraries, packages, among others, regardless of app architecture. This becomes exponentially challenging with serverless.
What you can do:
The first thing you can do is to avoid third-party packages with lots of dependencies. Instead, you can derive components from reliable official sources through secure links.
For example, if you run a Node.js application, use package locks or NPM shrink-wrap to make sure that all updates need to be reviewed before getting into your code.
Additionally, you can continuously use automated dependency scanners such as snyk.io or OWASP Dependency-Check to identify and fix vulnerabilities in third-party elements.
3) Use built-in solutions for user authentication

The significant number of events and functions that can be utilized is one of the more prominent features of a serverless architecture. As such, trying to input security authentication systems for each component can be a complex and highly-sensitive process.
What you can do:
To alleviate broken authentication, authenticate users and authorize their access to resources with built-in solutions like authorizers or AWS Cognito.
It’s important to note that while your layer authentication may work flawlessly, a malicious attacker can still access S3 buckets with public read access.
So, unless you’re using a bucket for storing images or a static website, never enable public read access. Or if you must store images or a static website, that bucket must only contain files related to those.
4) Be vigilant against wallet-busting attacks

This is another case where serverless’ key feature becomes a double-edged sword, this time when it comes to autoscaling and relatively new types of attacks known as Denial of Service (DoS) or Denial of Wallet (DoW).
DoS is basically an attack that saturates your scaling limits, flooding it with fake requests to create a traffic jam that makes your service unavailable for customers.
And when you set your concurrency limits high enough to avoid DoS, an attacker can then try to overwhelm your app to inflate your expenses.
What you can do:
You can set budget limits and alarms based on your current spending. Just keep in mind that this kind of protection can still cause a DoS attack and hackers can shut down your online business.
You can also put limits on the number of API requests in a given time window, allowing a client, for example, to make one call per second while blocking additional calls.
If you have API gateways that are internal and used only within other components, you can make them private so attackers can’t approach them.
Additionally, you can use tools like Cloudflare that provide security features like WAF and rate limiting.
5) Protect against data injection

At the highest levels, injection flaws occur when untrusted input is passed directly to an interpreter before it’s been evaluated or executed. And in serverless architecture, function event-data injections aren’t just limited to direct user input. Most serverless infrastructures provide a myriad of event sources that can trigger the execution of a serverless function.
These include things like cloud storage events, NoSQL database events, SQL database events, code changes, and HTTP API calls, among others. The thing is, each attack input could include different message formats, and various parts of these event messages can contain dangerous inputs. This makes the task of protecting the serverless functions complex.
What you can do:
You need to make sure that your protection tools are focused on code integrity, tight permissions and behavioural analysis. In terms of maintaining code integrity, you’ll need to regularly scan for vulnerabilities like third-party dependencies, configuration errors, and over-permissive roles.
When it comes to access and permissions, maintain least-privileged access for serverless functions and other services. So, say, if an AWS Lambda function needs to access a DynamoDB table, you need to ensure that it can only perform the specific action the business logic requires.
Lastly, use runtime protection to detect malicious event inputs and potentially anomalous function behaviour and limit each function’s ability to access files, hosts, the internet, and create processes.
The Future is Serverless
While there remain many challenges, serverless computing is only expected to grow in the next few years. It is expected to go beyond cloud computing and always be one step ahead.
These advancements can change the way you do your business, equipping it with smarter functionalities that can also reduce operational costs – two key things most businesses will be striving for in a post-pandemic world.

